X
A course pivotal to navigating the challenges of the digital world
The Cyber Security for Digital Leadership Program is an advanced, executive-level program for cyber professionals who want to develop their executive skills, c-suite stakeholder and board engagement, and become a leading voice when it comes to security. It is designed to help you develop and execute high-value strategies to reach cyber resilience quickly and make the important link between cyber strategy, business strategy, and business risk. In this course, you’ll learn how to explain to all levels of management, including both technical and non-technical executive leadership, why cybersecurity must be a priority. The long-term endeavour is that security and risk mitigation becomes a primary component of corporate strategy.

100% Live
synchronous course
Global Faculty
from elite institutes

UCLA Extension Certification
as a record of participation
Integrated Group Work
on real world projects
Overview
In today’s Information Age, as business, governments, Public Sector Units, financial institutions, and individuals converge on the digital market space, generation, collection, processing, storage, and data exchange has become an integral part of digital transaction and interactions. In parallel, cyber security threats and cyber-attacks by hackers exploiting vulnerabilities of an organization’s cyber security is a common phenomenon. As a result, cyber risk management has become a fundamental component of business operations and understanding and mitigating risk has become an essential skill for business leaders, thought leaders, analysts, as well as security and technology specialists
COVID-19 had made the world far more connected. While multiple entities are interacting on the digital channels, they are far more vulnerable to cyber risk. The demands on organization infrastructure to withstand cyber-attacks has increased considerably. Likewise, existing infrastructure, policies, practices and cyber security culture needs a relook in light of the new business practices and arrangements in the post COVID-19 era.
This program uses concepts, insights from industry experts to prepare you to address cyber security from an enterprise wide approach, keeping into account the external landscape and future changes within their markets.
This program aims to enable you to devise and implement a new cyber security initiative which is robust, strategically aligned to your business context and scalable in the post COVID-19 “New Normal “era
What you will learn:
The goal of this course is to provide an effective combination of theory and practice of cyber security concepts. Live lectures, industry insights and project work will provide a rich forum for virtual class discussions. You will assemble key insights on the following:
Upon completion of the program, you will be ready to apply your knowledge to lead strategic decision making to leverage Cyber Security technologies in your business.
Who should take this course?
This program will benefit you if
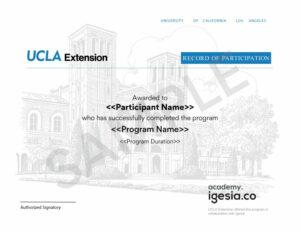
Upon successful completion of the course, you will be awarded a Record of Participation from the University of California, Los Angeles (UCLA) Extension.
You can share your Record of Participation in the Certifications section of your LinkedIn profile, on printed resumes, CVs, or other documents.
During the program you will have the chance to learn from world class faculty through live virtual lectures delivered from the USA on the Igesia learning platform. You will interact with industry executives and better understand ongoing trends in Indian and global business. You will be given the opportunity to work in groups on projects of relevance to your business contexts.
Orientation
You will be welcomed to the program and start connecting with fellow participants in the program and get an overview of the forthcoming program. You will also start forming teams and start considering questions to explore in your customized project work.
Module 1
Cyber security building blocks
The first module highlights the relevance of cyber threats and vulnerabilities impacting operational risk, litigation risk, and reputation risk. It discusses the key sources of cyber threat actors namely nation states, cyber criminals, and internal organizational threats, likely cyber-attack methods and the types of organizations or sectors they typically attack.
Live Virtual Session with Industry Expert
Module 2
Understanding cyber security technology
Examine how an organization’s systems, networks, and data are interconnected and the various methods of attack and countermeasures in each area. Understand the validity of implementing appropriate technologies to mitigate and secure the system, the network and the data – the three key elements of an organization prone to cyber risk.
Live Virtual Group Work led by Program Coach
Module 3
Cyber risk and the law
Identification of the most complex aspects of managing cyber risk, namely legal and compliance considerations at a state, national, and international level. Identify the impact of failing to take compliance considerations into account and explore the requirements of your own industry while learning to ask appropriate questions to assess your organization’s adherence to these legal and compliance requirements.
Live Virtual Session with Industry Expert
Module 4
Impactful leadership in managing cyber risk
This module looks at role of leadership in cyber security capacity building after identifying stakeholders in the governance structure of an organization , the user driven cyber culture and the socio-cultural fabric into account. It provides insights on global values, attitudes and practices of internet users impacting on-line privacy and trust issues. It describes why leaders have to be cognizant of user security mindset towards cyber attack risk mitigation. It describes the leadership role in boosting cyber security consciousness by designing best practices for implementing a cyber secure culture in an organization.
Live Virtual Group Work led by Program Coach
Module 5
Designing and implementing a cyber risk mitigation strategy
The last module focuses on three phases of a security breach, namely detection, communication, and containment of cyber breach. It focuses on processes and cyber threat mitigation implementation strategy, allocation of financial resources, and establishing an accurate metrics system to keep track of the security systems that have been put in place. It also dwells on the future direction of cyber security, considering the evolving landscape of artificial intelligence, big data, and geolocational data and the increased organizational risks that accompany these advances.
Post Program
Record of participation from the University of California, Los Angeles (UCLA) Extension
+ Knowledge updates + Alumni Community + Social interactions